Case Studies.
Our Case Study database tracks 18,927 case studies in the global enterprise technology ecosystem.
Filters allow you to explore case studies quickly and efficiently.
-
(2)
- (1)
- (1)
-
(1)
- (1)
-
(1)
- (1)
- (1)
- (1)
- (1)
- (1)
- (1)
- (1)
- (1)
- (1)
- (2)
Selected Filters
2 case studies
|
How Edge Computing Enables Predictive Maintenance of Valves
Infineon
Solution approach for monitoring production-critical ultrapure water valves with the aim of detecting possible failures at an early stage and better planning maintenance processes.
|
|
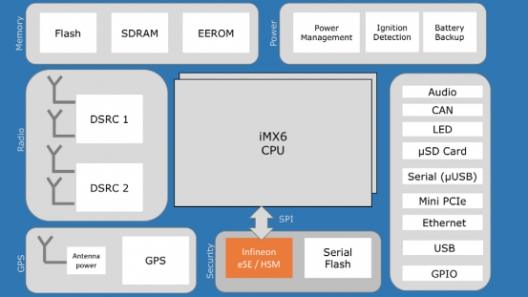
Infineon Supports Savari for HSM
Infineon
The V2X systems use a sophisticated Public Key Infrastructure (PKI)-based approach to facilitate trusted communication:V2X systems use Elliptical Curve Cryptography (ECC). Device must be able to securely and efficiently generate ECC keysThe random numbers generator must have high entropyRoot-certificates must be protected by usage of secured storageDevice must have tamper resistance, including physical attacksPrivate keys must have protection against side channel attacksPrivate keys must to be protected and used securely › V2X device are required to generate up to 40 messages per second. The signing latency must be low to support this frequency
|